Platform
Attack perimeter
Muscope|Risk's attack perimeter feature begins by identifying the company's domain and then locating its entire attack surface, including assets that are visible from the outside, such as websites, IPs, mail servers, networks, and ASNs. In addition, it analyzes the presence of company information on the darkweb and in data leaks and represents all of this information in a comprehensive graph that summarizes the company's attack perimeter.
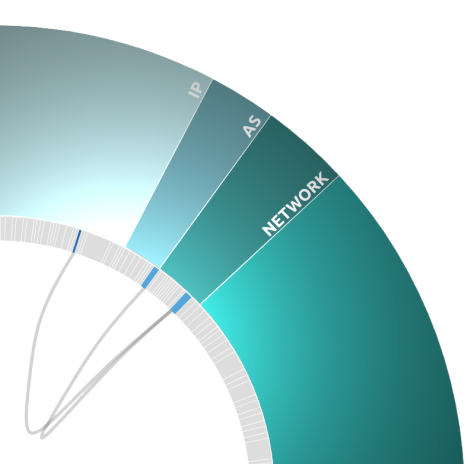
Our analysis is extremely detailed, and for each asset, we extract a wide range of information, including:
- IPs: open ports and the type of services that are exposed
- Websites: the type of applications installed and the libraries used, as well as the security of the certificate and javascript libraries
- Mail servers: the level of domain security on the mail server, such as DMARC and SPF configurations, etc.
- DNS servers: analyzing for security issues, such as zone transfers or adherence to best practices for DNS management
- Network: analyzing BGP routes to understand if the network is resilient to DDoS attacks
- ASNs: analyzing the size of the provider managing the autonomous system and the connections it has available, such as connections to Tier 1, Tier 2 providers or to Internet Exchanges around the world.